
Business, Compliance, cybersecurity, Dark Web, Disaster Recovery, Endpoint Detection and Response (EDR), Security, Security Breaches, Security Operations Center SOC
Outsourcing Your Cybersecurity, Safeguarding Your Digital Assets Small and medium-sized businesses (SMBs) often face the dilemma of whether to handle cybersecurity internally (DIY) or outsource it to specialized firms like JK Technology Solutions. In an increasingly...

Business, Business Computers, IT Consulting, Managed IT Services, Network Infrastructure, Tech Support
Managing IT In-House vs. a Managed Service Provider (MSP) A Comprehensive Comparison In the modern business landscape, the management of IT infrastructure is pivotal to operational efficiency and security. Small and medium-sized enterprises (SMEs) often face the...
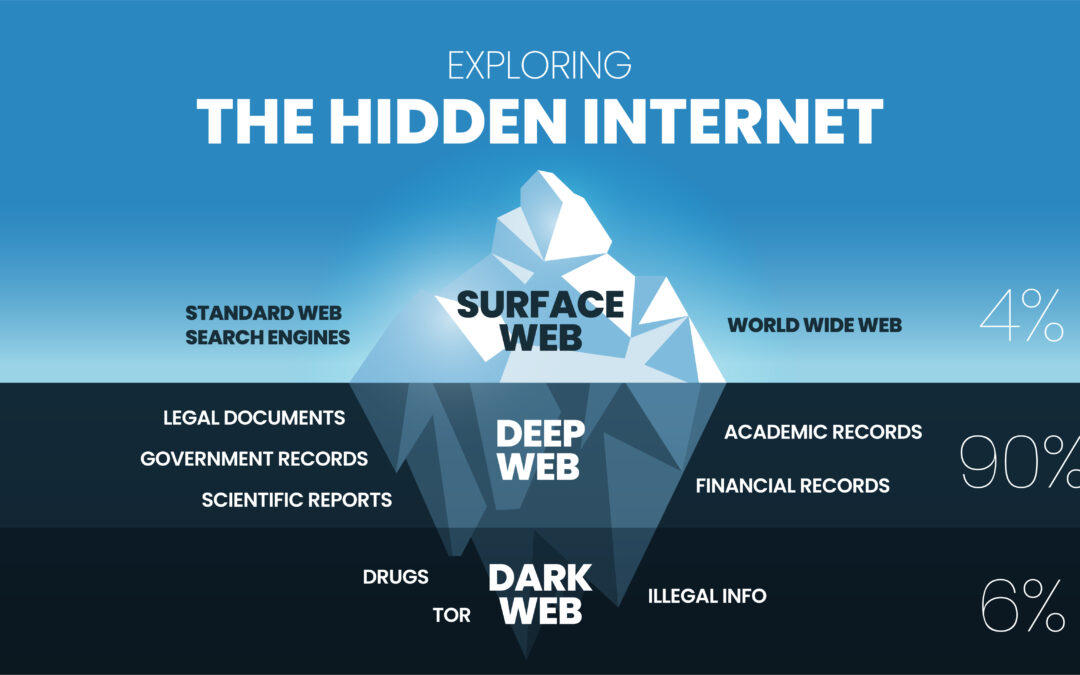
Compliance, cybersecurity, Dark Web, Security, Security Breaches, Uncategorized
Dark Web Monitoring Dark web monitoring is a service that scans the dark web for any mentions of your company’s sensitive information, such as login credentials, financial data, or intellectual property, that may have been compromised. The dark web is a part of...

Compliance, cybersecurity, Security, Security Operations Center SOC
Security Operations Center SOC A security operations center (SOC) is a centralized hub or command center that augments your overall IT & data security defense posture by harnessing the collective power of technology, processes, and people to aggregate, analyze,...
Business, Compliance, cybersecurity, Security Breaches
Predictive Analytics in Cybersecurity: Enhancing Compliance and Threat Detection In today’s digital landscape, Predictive Analytics is becoming an important component of your cybersecurity defense strategy. Safeguarding sensitive data and maintaining compliance...







